TL;DR:
-
Microsoft does not send subscription renewal calendar appointments.
-
Don’t accept long, multi-day calendar invites about “renewals” or “service disruption.”
-
Check the sender, if it’s not a Microsoft domain, it’s dodgy.
-
Never open an attached HTML/webpage file from an email or calendar invite.
-
If your Microsoft subscription is via your IT provider, invoices come from them, not random calendar invites.
-
If in doubt, delete and contact your IT support.
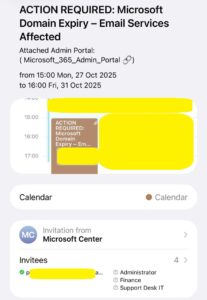
You open your phone, your calendar screams at you that your Microsoft 365 subscription is expiring, there’s a nice attachment, and one click later you’re staring at a “log in to renew” page that looks exactly like the real thing. Congratulations — you just met a calendar scam.
Here’s the simple truth: crooks have worked out that calendar invites often slip past spam filters and land straight in your calendar. They can attach a tiny HTML file (which runs locally on your device), pretend to be Microsoft, and hope you panic, type your credentials, and hand them your keys. Spoiler: Microsoft does not email you a “renew your subscription” calendar invite with an HTML attachment. If you see that, it’s fake. Burn it. Block it. Move on.
Why this trick works
Spam filters look for suspicious senders, spammy content and dodgy attachments. Calendar invites are often treated differently by mail servers and calendar apps, once accepted, the event is in your calendar and the spam filter effectively stops watching it. The scammers exploit that trust boundary.
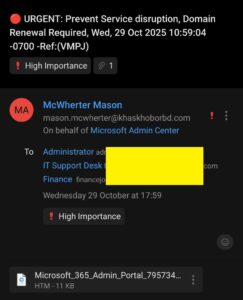
They also attach a small HTML file that runs locally. Because it’s a local file, it isn’t fetched from a remote server (so some scanners don’t flag it), and it can present a convincing fake login form that collects your username and password. The crook then uses those credentials to access your mailbox, files, or admin portals.
Also: urgency works. A calendar event saying “URGENT: Prevent Service disruption” plus a scary time pressure makes people click, and that’s exactly what the attackers bank on.
How to spot these scam calendar invites (quick checklist)
- Sender address: does it come from
microsoft.com,microsoftonline.com, or a recognisable Microsoft service? If not, treat it as hostile. - Event content: Microsoft won’t send a multi-day, all-day calendar appointment telling you to renew. Renewal notices are emails (if at all) and invoices come from your reseller/IT provider.
- Attachments: any web page (.htm/.html) attached to an email or invite = red flag. No legitimate company sends you a local HTML as an “invoice.”
- Links that ask for credentials: Microsoft uses proper OAuth flows and won’t ask for login details inside an attached file.
- Sudden invite from unknown organiser that appears in your phone/desktop calendar without being in your inbox, be suspicious.
What to do right now (practical steps)
If you see one of these invites:
- Do not open the attachment. Don’t click links in the event description either.
- Decline or delete the event, and remove any local copies. If it’s already accepted, delete it from the calendar immediately.
- Check Senders Details. Don’t focus on the Display Name, that can be anything, always check the sending email address.
- Contact your IT provider. If your subscription is through them, they’ll confirm invoices and can check whether any credentials were leaked. If you’re a TL Martin Ltd client, we’ll do this for you and secure anything that needs securing.
- If you suspect compromise: inform your IT support, and consider an account password reset and modern incident checks (audit logs, mailbox forwards, suspicious rules).
Final Thought
Scammers love confusion. They rely on panic, messy processes and people not knowing what a real Microsoft invoice looks like. That’s why having a trusted IT partner matters. At TLMartin Ltd we:
-
centralise billing and subscription management so your staff never get dodgy renewal calendar invites;
-
lock down email and calendar settings to stop junk appointments from landing in people’s diaries;
-
run quick checks if you suspect an account has been phished, password resets, MFA enforcement, mailbox rule audits and remediation;
-
and train your team with short, memorable guides so they won’t be the person who says “oh I’ll just click it.”
If you want us to tighten your Microsoft 365, and teach your team how to spot scammers, we’ll sort it. No drama, no fearmongering, just fewer surprises and the peace of mind of knowing someone sensible is watching your back.
Want us to take a look (now)? Tell us which account was hit and we’ll show you exactly what to do next.
