Breathe. You haven’t been hacked.
You’re sitting there, innocently sipping your morning brew, when ping!—an unexpected email from Microsoft arrives.
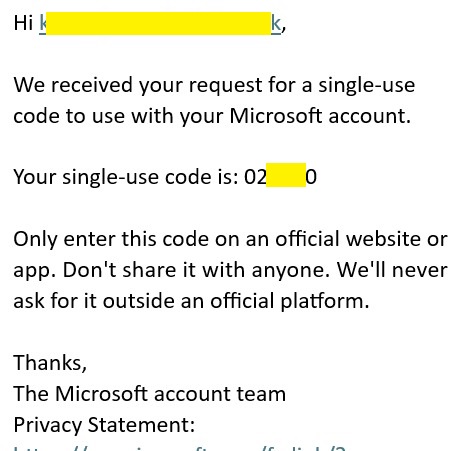
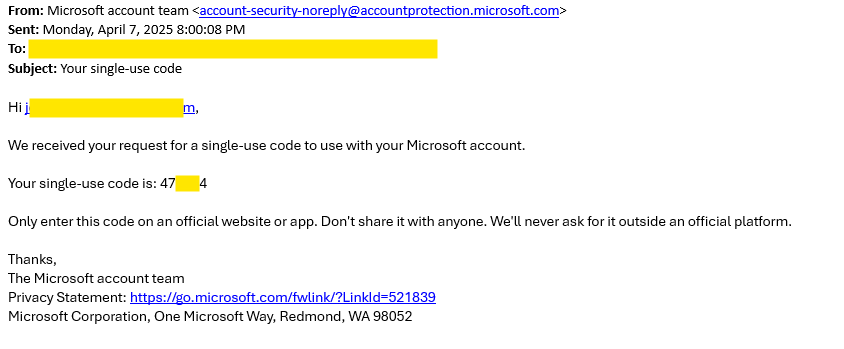
Subject: Your Single Use Code
Immediate Thought: “OMG! Someone’s in my account!”
Reality Check: No you haven’t.
Let’s break it down. You’re not alone. This little surprise is hitting inboxes across the land, and while it feels like a digital burglar is rummaging through your virtual underpants drawer, the reality is far less dramatic (but still worth paying attention to).
So What Is This Email?
It’s actually a legit email from Microsoft. Yes – genuine sender, correct domain, DMARC in place. All the good stuff.
So, should you be panicking because this means someone’s trying to hack your account?
Well, not exactly. What’s really happening is… Someone’s Testing Your Car Door Handles
Think of your Microsoft account like a parked car.
The would-be hacker hasn’t smashed a window or picked the lock—they’ve just walked past, tugged on the handle, and checked if it opens. That’s it.
When someone goes to live.com, types in your email, and attempts to log in, Microsoft may (depending on your settings) automatically send a Single Use Code to your email. You didn’t request it, but it’s been triggered as part of that attempt.
Important: They don’t have your password, they haven’t logged in, and they’re not reading your files.
This is reconnaissance. They’re seeing how fortified your digital castle is. Do you have MFA? Authenticator App? Email-only login? Are you using the same old password you used for MySpace?
Why Would They Do This?
- They Have (or Think They Have) One of Your Passwords
Maybe your password’s been leaked in a breach or phished from you during a weak moment (we’ve all been there—“Free Pizza Coupon” is hard to resist).
Now they’re trying to see if it still works. And if you use the same password across multiple sites… well, you’ve handed them a skeleton key.
🔐 Fix It Tip: Use unique passwords for every site. Better yet, get a password manager and turn every login into a Fort Knox entry protocol.
- They’re Just Seeing What You’ve Got
If they trigger a login attempt and see that Microsoft Authenticator is one of your methods, they’ll know you’ve got MFA turned on.
Good news: MFA is your superhero cape in these situations. Even if they had your password, they’d still need that magical second factor to get in.
- They Want to Trick You Into Giving Up the Code
This is the social engineering bit. They cause panic, then pounce—maybe by following up with a phone call pretending to be Microsoft support.
“Hi, we’ve seen a security breach on your account. Can you please read us that code to verify you’re the owner?”
🚨 Red Flag Alert: Microsoft will NEVER call you and ask for this code. If they do, you’re not talking to Microsoft – you’re talking to Scammy McScammerface.
- They Want to Cause Chaos
This one’s subtle. Maybe the scammer just wants you to block the sender—which happens to be Microsoft.
Now you’ve blocked accountprotection.microsoft.com or the entire microsoft.com domain.
Congrats – you just locked yourself out of receiving legit emails from Microsoft: invoices, renewals, login codes, security alerts… gone. 🙈
What Should You Actually Do?
- Check your password: If it’s old, weak, or has shown up in a breach, change it now.
- Make sure MFA is enabled: If you haven’t already, set it up. It’s the “deadbolt” to your “car door.”
- Don’t block Microsoft: Blocking these emails is like putting earplugs in when someone shouts “FIRE!”
- Don’t panic. You’re on a list. It’s like marketing – if you’ve received one, you’ll probably receive a few. It’s your turn in the scammer spotlight. They’ll move on soon enough.
One Last Thing: Don’t Block Scam Emails
I get it, it’s satisfying to hit Block and feel like you’ve defeated the bad guys. But here’s the problem:
- Scammers rarely use the same address twice
- Most get into personal email domains like gmail.com, outlook.com, or hotmail.com
- They may just spoof legitimate emails or be sending from a hacked business account
You might end up blocking actual customers, prospects, or your Aunt Marge
And if you’re a B2C business? Blocking common domains = 🚫 sales, 🚫 leads, 🚫 grandma’s cookie recipe.
TL;DR:
Getting a Microsoft Single Use Code email you didn’t request? Don’t panic – you haven’t been hacked. Scammers are just testing if your account is vulnerable (like trying your car door handle). They can trigger these codes by entering your email at login, but they can’t access anything unless you hand over the code or have weak security.
✅ Make sure you’ve got strong, unique passwords
✅ Turn on Multi-Factor Authentication (MFA)
❌ Don’t block Microsoft emails – you could lock yourself out or miss important alerts
You’re probably just on a scammer’s list for now, but take this as a reminder to tighten your digital defences.
The Microsoft Single Use Code email isn’t a reason to freak out—it’s just your car door being gently jiggled. But it’s a great nudge to make sure your digital locks are solid.
Strong password?
MFA turned on?
Not blocking vital senders?
Then you’re doing it right.
And if you want to go a step further, request a free Dark Web scan to see what passwords or accounts of yours might be floating around in shady circles:
https://tlmartin.ltd.uk/services/dark-web-report-request/
Stay smart, stay safe, and always read those emails before hitting block!
